Haystacks and Post-Quantum Crypto
Spice Labs surveys applications using cryptographic hashes to provide on-demand, comprehensive maps, enabling confident scoping, modernization planning, and breach response with accuracy and measurability.
Haystacks and Post-Quantum Crypto
Our IT landscape is haystacks as far as the eye can see.
How did those haystacks get there? Maybe it was a series of acquisitions. Maybe it was the “almost complete” cloud migration.
But what’s more important… what needles are in which haystacks?
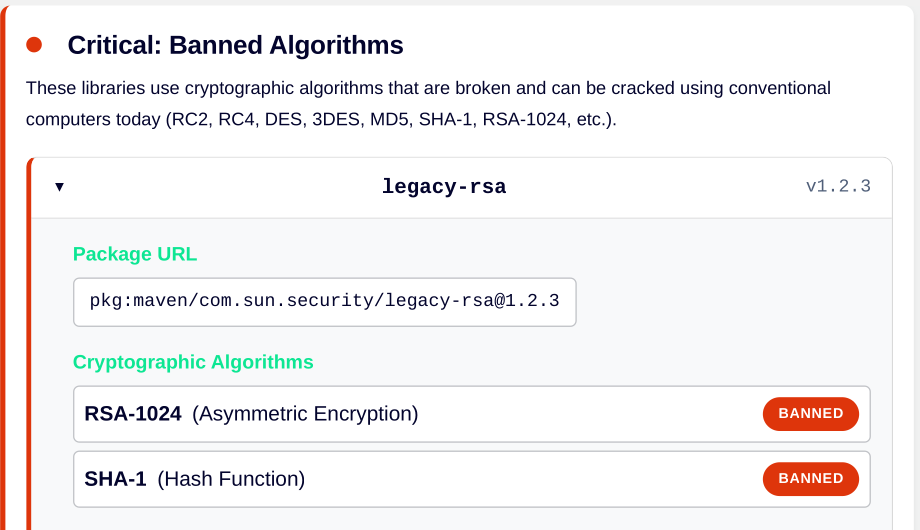
A set of needles we’re starting to look for are the right and wrong cryptography libraries.
Post Quantum Cryptography
The time is now to begin addressing the eventual arrival of “Q-Day” – the moment when a cryptographically capable quantum computer achieves the capability to crack current encryption algorithms. Although experts estimate that milestone won’t arrive until the early 2030s, others such as Gartner predict existing cryptography will be unsafe by 2029.
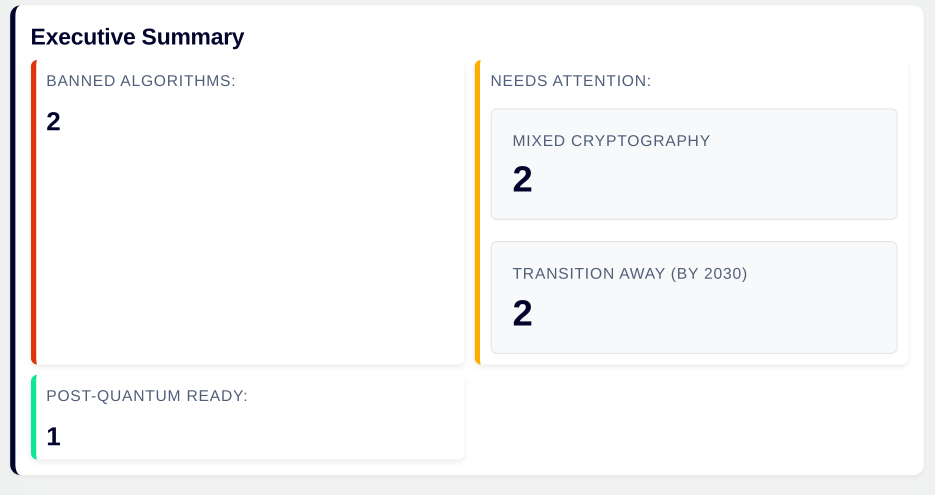
Governments have already set deadlines for upgrading systems used by their agencies; and regulators are imposing similar deadlines for at-risk sectors such as financial services and healthcare. Upgrading to post-quantum crypto proof solutions begins by first identifying where at-risk encryption algorithms are present in applications. Spice Labs is an ideal tool for surveying a software stack, pinpointing the issue, and tracking progress towards post-crypto compliance.
Simply use Spice Labs’ Surveyor to build Artifact Dependency Graphs (ADGs) of docker containers, JAR files, and even VM images. No need to change engineering process.
Securely upload to Spice Labs’ Topographer. Click a button and get reports:
The Power of Math
Spice Labs uses to power of math, specifically Merkle Trees, just like Git. Spice Labs can scale to millions of artifacts. In fact, Spice Labs has a database that captures the connections across Java open source, Debian, and Ubuntu. 55M packages results in a 13B node graph… all served from a single, commodity box.
Surveyor builds ADGs of post-build artifacts. No need to change engineering process. Just point Surveyor at Docker images, JAR files, and even VM images.
If you want to integrate Surveyor into your CI pipeline, there’s a GitHub Action for that.
Nested Haystacks
The power of math… the power of Artifact Dependency Graphs, extends beyond scalability.
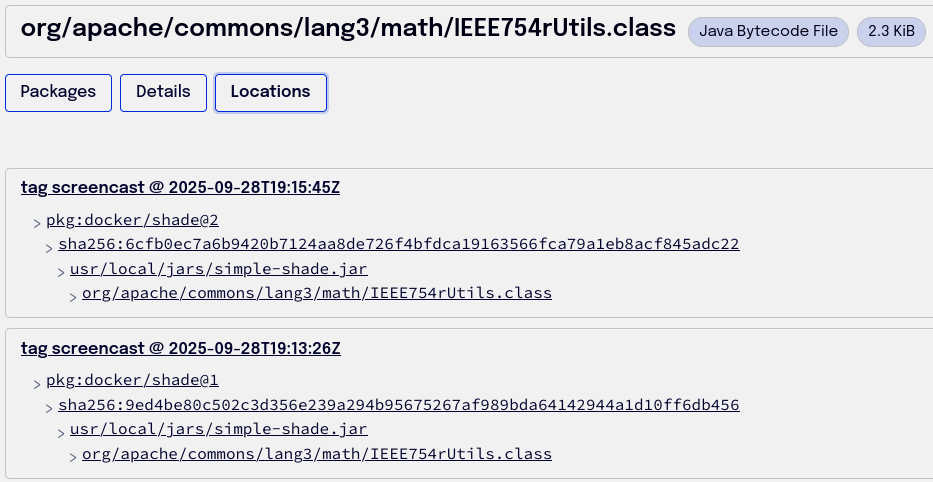
Spice Labs captures nested relationship. This means an RC2 encryption class that an engineer vendored into a JAR will be discovered when Surveyor does its thing.
Further, Topographer’s query function answers the question, “show me all the artifacts that contain class X or package Y.”
Make the Next log4shell Boring
There’s going to be another log4shell.
Those of us who lived through December 2021 would have loved to have what Spice Labs is delivering today: a database that can be queried to show every artifact that contains a particular version of a library.
Spice Labs makes the next log4shell a boring database query… well… followed by some remediation.
More importantly, knowing the assets that are vulnerable within minutes of a critical vulnerability being announced gives security teams a punch-list of what to secure and what to wrap “application firewalls” around.
Knowing your Systems
Because Spice Labs gives you a database of what’s in all the haystacks across your enterprise, you have the the situational awareness to chart your course and make the right decisions.
Start surveying to plan for Post Quantum Crypto today. Those same surveys… that same database… will have a myriad of positive applications across both the security and engineering side of your organization.